| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 | 31 |
- Interface
- error
- nextJS
- node.js
- blockchain
- useState
- middleware
- web
- express.js
- solidity
- 기준
- Ethereum
- CLASS
- JavaScript
- hardhat
- REACT
- HTML
- evm
- built in object
- SSR
- typeScript
- CSS
- Redux
- API
- graphQL
- bitcoin
- Props
- tailwindcss
- concept
- 삶
- Today
- Total
ReasonJun
Bitcoin : whitepaper (2) 본문
Incentive
→ By convention, the first transaction in a block is a special transaction that starts a new coin owned by the creator of the block. This adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them.
→ The incentive can also be funded with transaction fees.
→ Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and be completely inflation free.
Reclaiming Disk Space
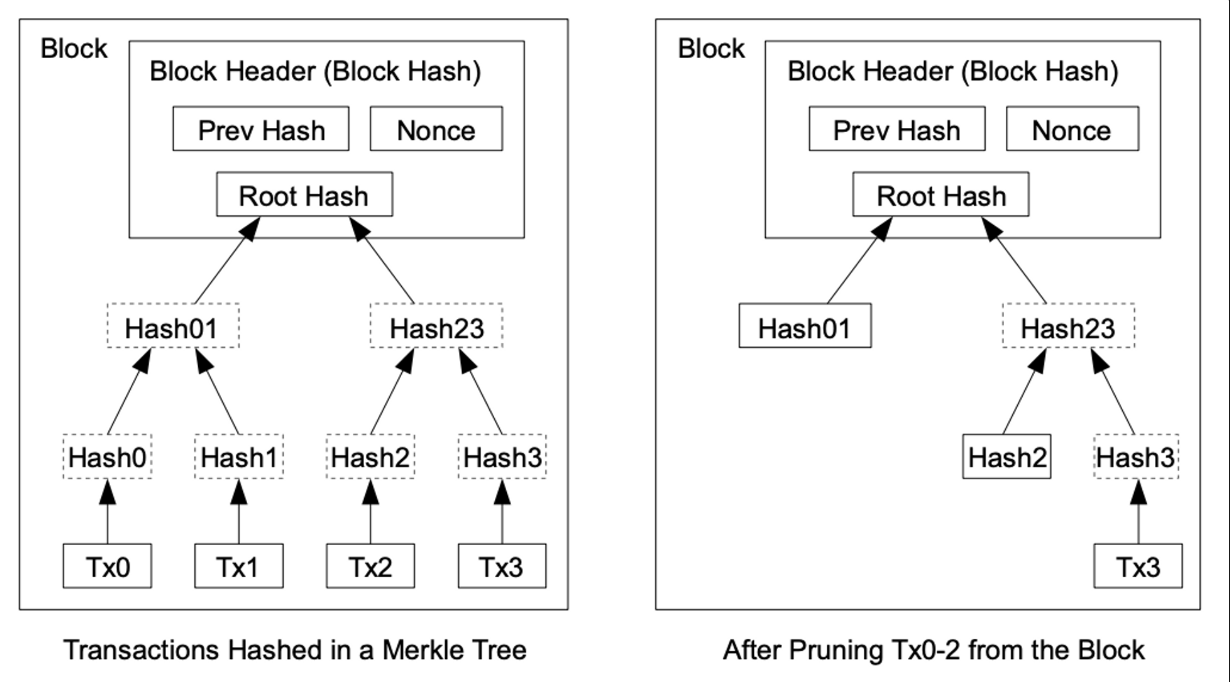
Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block's hash, transactions are hashed in a Merkle Tree [7][2][5], with only the root included in the block's hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored.
Simplified Payment Verification
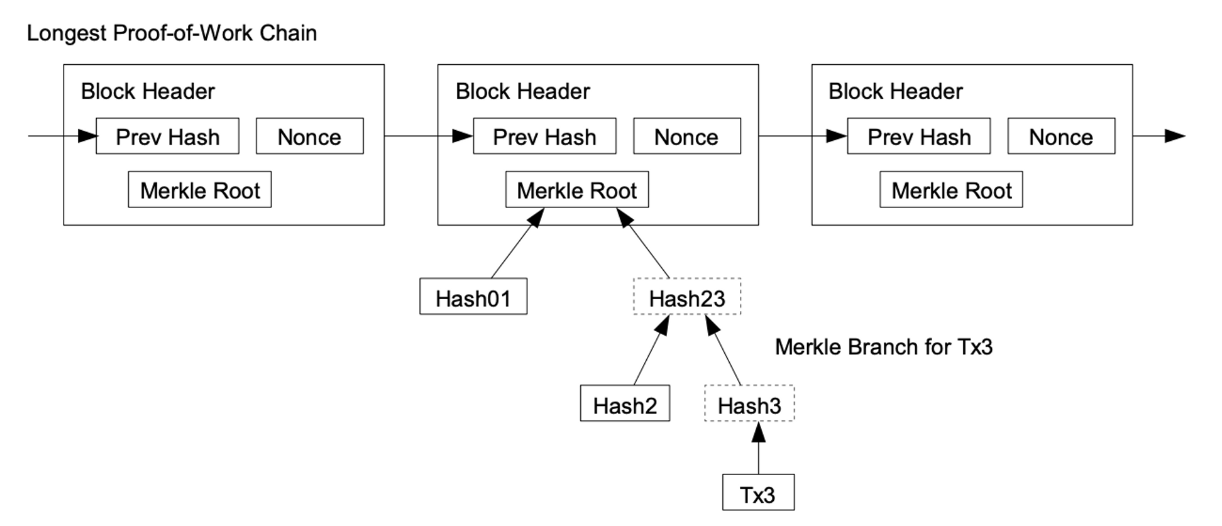
It is possible to verify payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he's convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it's timestamped in. He can't check the transaction for himself, but by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it.
Combining and Splitting Value

→ To allow value to be split and combined, transactions contain multiple inputs and outputs.
→ Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender.
→ It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here.
Privacy
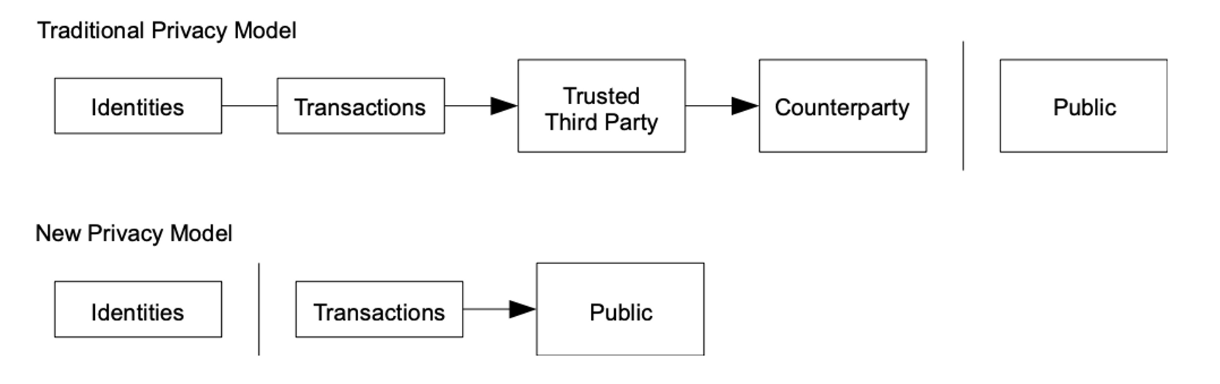
→ The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party
→ The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in anoth er place: by keeping public keys anonymous.
→ The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone.
→ As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner.
Calculations

→ Given our assumption that p > q, the probability drops exponentially as the number of blocks the attacker has to catch up with increases.

Conclusion
The proposed system aims to enable electronic transactions without relying on trust. It utilizes a framework based on digital signatures for coins to ensure ownership control but addresses the double-spending problem through a peer-to-peer network and proof-of-work. In this network, transactions are recorded in a public history that becomes computationally impractical for attackers to alter if honest nodes control the majority of CPU power. The network operates with minimal coordination, allowing nodes to join or leave at will, and it doesn't require node identification. Nodes express their acceptance of valid transactions by working on extending them and reject invalid ones by refusing to work on them, making it a robust and decentralized consensus mechanism capable of enforcing rules and incentives.
'Blockchain > Bitcoin' 카테고리의 다른 글
| Bitcoin : gRPC vs HTTP API (0) | 2023.09.17 |
|---|---|
| Bitcoin : Merkle Tree (0) | 2023.09.17 |
| Bitcoin : ECDSA (Elliptic Curve Digital Signature Algorithm) (0) | 2023.09.17 |
| Bitcoin : Cryptographic systems (RSA / ElGamal Encryption / Hash Encryption) (0) | 2023.09.17 |
| Bitcoin : whitepaper (1) (0) | 2023.09.16 |


